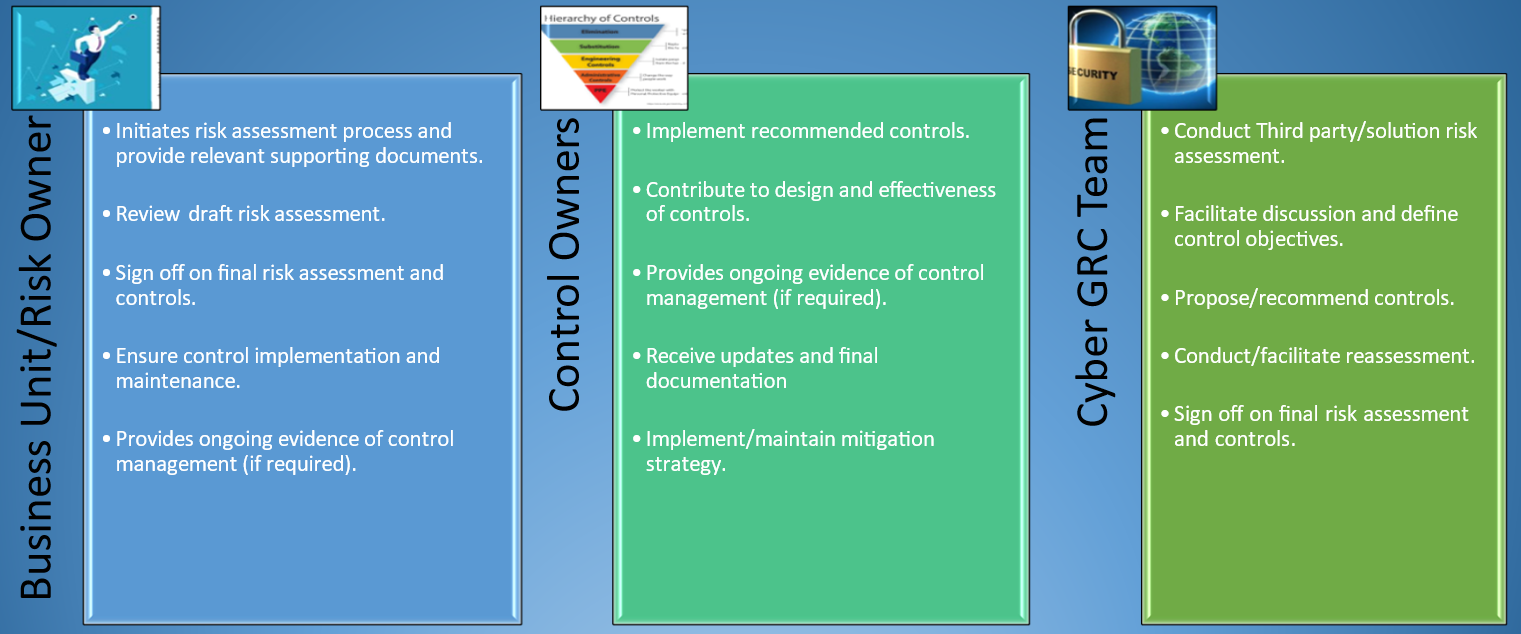
UniSA cyber risk assessments are essential processes for business stakeholders, as they help identify and mitigate potential security risks associated with third-party vendors and their technology solutions. These assessments ensure that external partners and new technologies align with the institution's security standards and operational requirements. By identifying and addressing business risk, stakeholders can make informed decisions to better protect university data systems, staff and students’ privacy, thereby fostering a secure and resilient educational environment.
There are two types of cyber risk assessments that can be performed for business stakeholders:
Third-Party Vendor Assessment (TVA) is the process of evaluating the security, compliance, and operational risks that external vendors or partners may pose to an organization’s data, systems, or business operations.
Solution Risk Assessment (SRA) is the process of identifying, evaluating, and mitigating potential risks associated with the design, implementation, or integration of a specific technology solution introduced to an organisation’s operational environment.